Code of federal regulations provisions pertaining to certain information access aspects of e o.
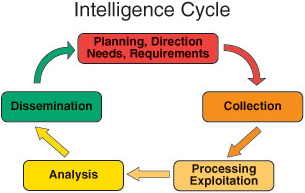
Steps of the information security program lifecycle classification dissemination.
It is initially issued by original classification authorities or ocas to document and.
In order to obtain a security guard license in new york state unarmed you must complete the following steps.
What are the steps of the information security program life cycle.
Security classification guidance is any instruction or source that sets out the classification of a system plan program mission or project.
Classification safeguarding dissemination declassification and destruction.
Are the steps of the information security program lifecycle.
Added 44 days ago 8 18 2020 11 26 51 pm.
22 cfr 9 sets forth the department s regulations regarding classification and declassification of national security information including derivative classification and classification challenges.
Classification safeguarding dissemination declassification and destruction.
It covers the information security program lifecycle which includes who what how when and why information such as a document like me is classified known as classification protected known as safeguarding shared known as dissemination downgraded declassified and.
Are the steps of the information security program lifecycle.
Log in for more information.